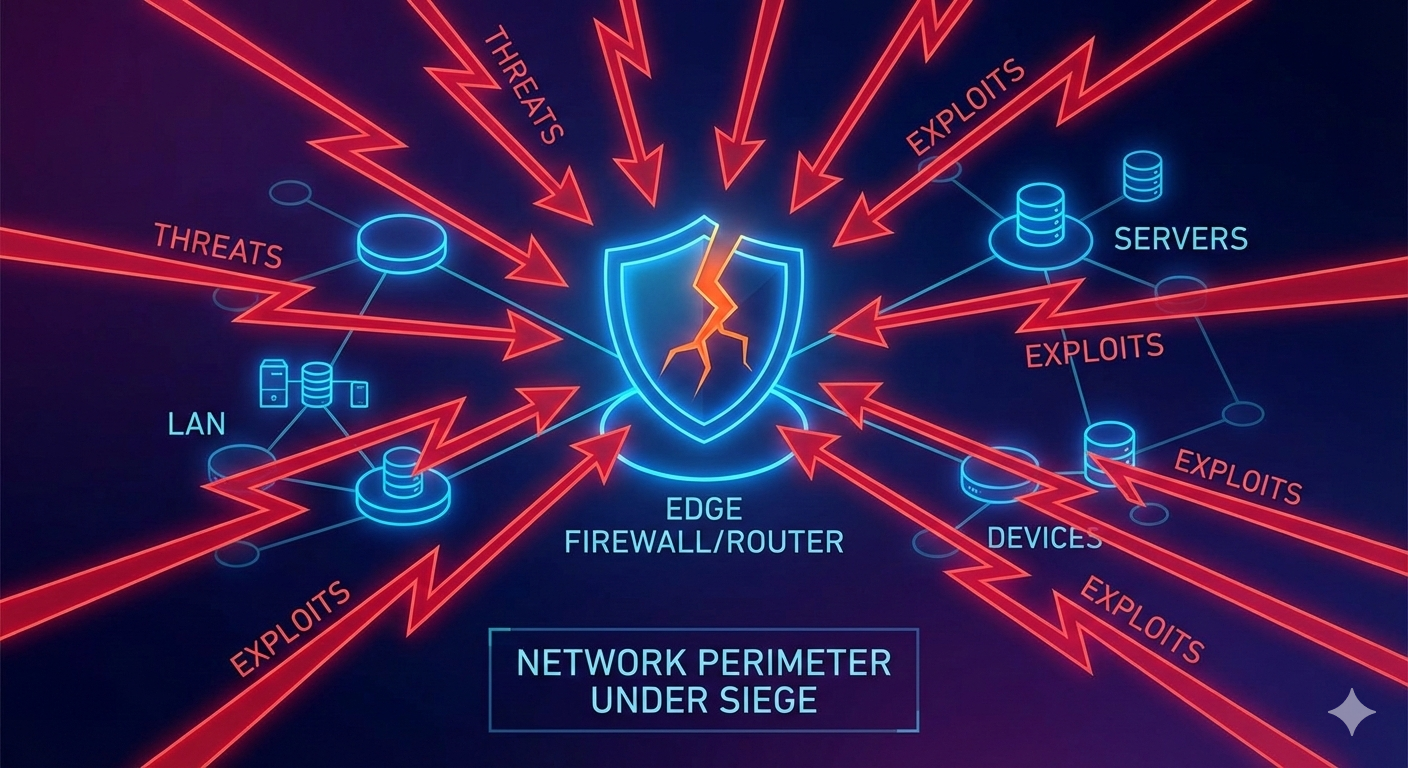
CISA's Edge Device Mandate Is a Wake-Up Call: Why Your Network Perimeter Is Your Biggest Liability in 2026
The Compounding Effect of AI-Powered Threats
The 2026 threat landscape is also being reshaped by the rapid adoption of autonomous AI agents in the enterprise. According to research cited in the World Economic Forum's Global Cybersecurity Outlook 2026, AI adoption is accelerating faster than security frameworks can adapt, creating a widening "cyber inequity" across organizations.
Palo Alto Networks' Wendi Whitmore described the situation starkly: AI agents are becoming "the new insider threat" because they operate with privileged access, make autonomous decisions, and can be manipulated through prompt injection or misuse of tools. When you combine these AI-driven risks with unpatched, end-of-life infrastructure at the network edge, the attack surface doesn't just grow — it compounds exponentially.
The Real-World Risk: What This Looks Like in Practice
[Anonymized Pattern — Composite Based on Industry Observations]
Consider a mid-sized healthcare network operating across four clinic locations. Their perimeter is secured by a mix of firewalls from two vendors — one set deployed in 2018, the other in 2020. The 2018 units reached end-of-support in late 2024. The IT team, stretched thin and constrained by budget cycles, planned replacements for the next fiscal year.
In the interim, a vulnerability disclosed in December 2025 affected the legacy firmware. No patch was issued because the vendor had already ended support. Within weeks, the organization experienced anomalous outbound traffic patterns consistent with data exfiltration. The attackers had established persistence through the unpatched edge device and moved laterally into clinical systems.
This pattern — deferred replacement, missed vulnerability windows, and lateral movement from the edge — is precisely the scenario CISA's directive aims to prevent. Neglecting edge device lifecycle management can lead to breaches, data exfiltration, and operational disruptions across industries such as retail, manufacturing, and healthcare, emphasizing the need for immediate action.
A Practical Framework: The Edge Device Security Lifecycle
Whether or not you fall under CISA's directive, adopting its phased approach as an internal standard is a sound strategy. Here is a five-phase framework adapted from the BOD 26-02 timeline that any organization can implement:
Phase 1: Discover and Inventory (0–90 Days)
Conduct a complete asset discovery of all edge-facing devices. This includes not only firewalls and routers but also wireless access points, SD-WAN appliances, IoT gateways, VPN concentrators, and load balancers. Cross-reference each device against the manufacturer's published end-of-life and end-of-support dates.
Recommended approach: Use network scanning and asset management tools (such as Rumble/runZero for network discovery, or your existing CMDB if properly maintained) combined with manual verification for OT/IoT environments where active scanning may be unsafe.
Phase 2: Risk-Rank and Prioritize (30–60 Days, Overlapping)
Not all end-of-life devices pose the same risk. Prioritize based on three factors: exposure (is it internet-facing?), criticality (does it protect sensitive data or regulated environments?), and exploitability (are there known CVEs with public exploit code?).
Devices that are internet-facing, unpatched, and protecting regulated data (HIPAA, PCI-DSS, SOC 2 environments) should be addressed first.
Phase 3: Remediate or Replace (Ongoing, 3–12 Months)
For devices still receiving vendor support, apply all available patches and firmware updates immediately. For end-of-support devices, begin procuring and deploying replacements. Where immediate replacement is not possible, implement compensating controls such as network segmentation, enhanced monitoring, access restrictions, and virtual patching via IPS/IDS rules.
Phase 4: Implement Continuous Lifecycle Management (12–24 Months)
Build a process — not a one-time project — for tracking device lifecycle status. Integrate vendor end-of-support dates into your asset management workflows. Set automated alerts for devices approaching end-of-support 12 months in advance. This is the most commonly skipped phase and the one that prevents you from ending up back where you started.
Phase 5: Align With Zero Trust Architecture
End-of-life device remediation should not exist in a vacuum. It should be part of a broader migration toward Zero Trust principles: microsegmentation, identity-based access controls, continuous verification, and the assumption that the perimeter is already breached. Edge devices that cannot support modern security protocols (TLS 1.3, mutual authentication, encrypted management interfaces) should be treated as architectural debt.
Common Mistakes That Amplify This Risk
Based on years of consulting across healthcare, retail, and professional services environments, these are the patterns I see repeatedly:
Mistake 1: Treating edge device replacement as a capital expenditure problem only. Yes, hardware costs money. But the calculation changes entirely when you factor in the cost of a breach. [STAT NEEDED: average price of a breach attributed to unpatched edge devices vs. total cost of proactive device lifecycle management — would strengthen ROI argument here.]
Mistake 2: Assuming compensating controls are permanent solutions. Network segmentation and virtual patching are bridges, not destinations. Threat actors evolve. Compensating controls degrade over time as new vulnerabilities emerge in adjacent systems.
Mistake 3: Overlooking branch offices and remote sites. Central data centers get attention. Branch offices, retail locations, and remote clinics often run the oldest hardware with the least visibility.
Mistake 4: No executive reporting on device lifecycle status. If your CISO or CIO doesn't receive a quarterly report showing edge device inventory, support status, and risk scores, this is an invisible problem until it becomes a crisis.
Mistake 5: Ignoring the AI agent overlay. As organizations deploy autonomous AI agents that interact with network resources, those agents inherit the security posture of the infrastructure they traverse. An AI agent routing through an unpatched legacy VPN concentrator doesn't make that concentrator more secure — it makes the agent's actions less trustworthy.
The Broader 2026 Context: Why This Matters Now More Than Ever
This week's CISA directive does not exist in isolation. It is one signal in a larger pattern:
- The World Economic Forum's Global Cybersecurity Outlook 2026 report highlights that 23% of public-sector organizations report having "insufficient cyber-resilience capabilities," and that geopolitical fragmentation is widening global capability gaps.
- Tines' Voice of Security 2026 report found that while 99% of SOCs now use AI in some capacity, manual workloads still consume a significant portion of team time, creating burnout and attrition risks that directly impact the ability to maintain infrastructure hygiene.
- NGINX web traffic hijacking campaigns disclosed this week by Datadog Security Labs demonstrate that attackers are actively targeting standard web infrastructure components, not just high-profile enterprise products.
- A Substack data breach disclosed on February 3, 2026 — involving an intrusion from October 2025 that went undetected for four months — underscores how delayed detection compounds the impact of infrastructure vulnerabilities.
- Italy blocked Russian cyberattacks targeting the Winter Olympics, and Russia's APT28 ramped up operations against Ukraine, reinforcing that nation-state threat activity remains at elevated levels across all sectors.
The convergence is apparent: adversaries are industrializing their operations, AI is expanding the attack surface, and the foundational infrastructure — the edge — is often the weakest link in the chain.
What You Should Do Monday Morning
If you're a CISO, IT Director, or technology leader reading this, here are five actions to take immediately:
- Request a complete inventory of edge devices from your infrastructure team this week. If one doesn't exist, that's your first finding.
- Cross-reference every edge device against its vendor's published end-of-life schedule. This data is publicly available from every major networking vendor.
- Identify any internet-facing device that is past end-of-support. These are your critical-risk items.
- Brief your executive leadership or board. Frame this around CISA's directive as a regulatory signal — even if you're not a federal agency, auditors and cyber insurers are watching.
- Engage your managed security provider or consulting partner to conduct an independent edge device risk assessment if internal resources are constrained.
The Bottom Line
CISA's BOD 26-02 is not just a compliance requirement for federal agencies. It's a public declaration that the security community has known for years: the network edge is the soft underbelly of enterprise security, and organizations that neglect device lifecycle management are building on a crumbling foundation.
In 2026, with nation-state actors actively exploiting these devices, AI agents multiplying the consequences of infrastructure weaknesses, and the regulatory landscape tightening, the cost of inaction has never been higher.
The good news? The remediation path is clear, proven, and achievable. The question is whether your organization will treat it as a priority before it becomes an incident.
Sources
- CISA BOD 26-02 — Binding Operational Directive on End-of-Support Edge Devices (February 5, 2026)
- BleepingComputer: https://www.bleepingcomputer.com/news/security/cisa-orders-federal-agencies-to-replace-end-of-life-edge-devices/
- The Record (Recorded Future): https://therecord.media/cisa-gives-federal-agencies-one-year-end-of-life-devices
- CyberScoop: https://cyberscoop.com/cisa-bod-directive-unsupported-edge-devices-firewalls-routers/
- Cybersecurity Dive: https://www.cybersecuritydive.com/news/cisa-edge-devices-binding-operational-directive/811539/
- Help Net Security: https://www.helpnetsecurity.com/2026/02/06/cisa-orders-us-federal-agencies-to-replace-unsupported-edge-devices/
- Nextgov/FCW: https://www.nextgov.com/cybersecurity/2026/02/cisa-orders-agencies-patch-and-replace-end-life-devices-citing-active-exploitation/411227/
- Federal News Network: https://federalnewsnetwork.com/cybersecurity/2026/02/cisa-tells-agencies-to-identify-upgrade-unsupported-edge-devices/
- Asian Cyber-Espionage Campaign Across 37 Countries — Palo Alto Networks Unit 42 Research (February 5, 2026)
- Claims Journal / Bloomberg: https://www.claimsjournal.com/news/national/2026/02/05/335524.htm
- Amaranth-Dragon / APT 41 Campaign Targeting Southeast Asia — Check Point Research (February 2026)
- The Hacker News: https://thehackernews.com/
- BleepingComputer: https://www.bleepingcomputer.com/
- AI Agent Security & Insider Threat Predictions for 2026
- Palo Alto Networks 2026 Predictions: https://www.paloaltonetworks.com/blog/2025/11/2026-predictions-for-autonomous-ai/
- The Register — Interview with Wendi Whitmore: https://www.theregister.com/2026/01/04/ai_agents_insider_threats_panw/
- Dark Reading — 2026 Agentic AI as Attack Surface: https://www.darkreading.com/threat-intelligence/2026-agentic-ai-attack-surface-poster-child
- World Economic Forum — Global Cybersecurity Outlook 2026 (January 2026)
- Tines Voice of Security 2026 Report
- NGINX Web Traffic Hijacking Campaign — Datadog Security Labs (February 5, 2026)
- The Hacker News: https://thehackernews.com/
- Substack Data Breach Disclosure (February 3, 2026)
- The Cyber Express: https://thecyberexpress.com/tce-weekly-roundup-february-2026/
- CISO Priorities in 2026 — Robert Hannigan, Enterprise Times (February 5, 2026)
- Weekly Cybersecurity Roundup — DataBreachToday (February 5, 2026)