The Week Ransomware Went Nuclear: Qilin's Rampage and What September 29-October 1 Revealed About 2025's Cyber Crisis
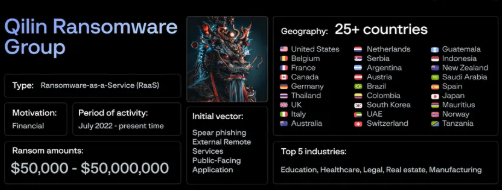
The Qilin ransomware group claimed dozens of new victims over the weekend. ZTE showcased AI-powered 5G anti-fraud technology in Beijing, and the ransomware landscape shifted dramatically as we closed out September 2025. Here's what happened that every IT director needs to understand.
Monday Morning's Nightmare: The Qilin Ransomware Tsunami
Let me start with what should have every IT director's attention this morning. Over the September 29-30 weekend, the Qilin ransomware group went on an unprecedented claiming spree, adding multiple high-profile victims to their data leak site.
The Weekend Victims That Tell a Story:
On September 30 alone, Qilin publicly listed attacks against organizations across multiple sectors, including travel agencies, water utilities, park districts, and asset management firms. What caught my attention wasn't just the volume—it was the systematic targeting pattern.
Among the victims discovered on September 30, 2025: Hoffman Estates Park District, Lakehaven Water and Sewer District, Mobidic Asset Management, and Spanish travel agency Pangea. But here's what the headlines aren't telling you: Qilin has topped the charts as the most active ransomware group, claiming 18.4% of 2,164 ransomware attacks since April 2025.
Why This Weekend Was Different:
The group isn't just encrypting data anymore—it's running a sophisticated business operation with features that would make legitimate SaaS companies jealous.
Throughout 2025, Qilin has added spam campaigns, DDoS attack capabilities, automated network propagation, ransom negotiation from within the affiliate panel, and even "in-house journalists" to assist affiliates with blog posts and pressure during negotiations.
The Technical Reality:
Qilin performs double extortion with rapid, high-speed encryption and deletion of backups, with damages ranging from $6 million to $40 million per victim. It primarily affects healthcare and government agencies. That's not a typo—single organizations are losing tens of millions of dollars in individual attacks.
The Pattern No One's Talking About: Qilin's Rise From the Ashes of Others
Qilin has vaulted into dominance after benefiting from an influx of affiliates following RansomHub's shutdown at the start of last month. This isn't organic growth—this is ecosystem consolidation.
What the Data Shows:
Qilin's data leak site disclosures have more than doubled since February 2025, with 72 claimed victims in April alone, surpassing Akira, Play, and Lynx. But the acceleration over September 29-30 suggests they're not slowing down.
The Business Model That's Working:
Qilin operates as Ransomware-as-a-Service (RaaS), which means it provides the infrastructure while affiliates perform the actual attacks. Think of it as the AWS of cybercrime—an industrialized ransomware deployment.
Qilin provides data storage for affiliates, automated network propagation, and even automated ransom negotiation tools. This is enterprise-grade criminal infrastructure.
Monday's Silver Lining: AI-Powered Defense From Beijing
While ransomware dominated the weekend news, one bright spot deserves attention. On September 30, 2025, ZTE Corporation and China Mobile Henan Branch showcased AI+ 5G New Calling Service at PT Expo China in Beijing. The service features AI anti-fraud capabilities that build security defense boundaries against fraud to protect users' property in real time.
Why This Matters:
The technology demonstrates how AI can be weaponized for defense, not just offense. The solution earned first prize in the ICT China (2025) Case Collection for "AI Anti-Fraud Construction of Security Defense Line".
For those of us in enterprise security, this represents a practical application of AI that goes beyond the hype. Real-time fraud detection integrated into communications infrastructure could become a model for how we defend against social engineering attacks.
The Numbers That Should Concern Every Organization
Let me put this weekend's events into a broader context with data that came out alongside the Qilin attacks:
The Ransomware Ecosystem in Late 2025:
- Qilin leads with 18.4% of all attacks since April 2025
- Sinobi has rapidly risen to third place after only two months in existence, claiming 41 victims
- Multiple groups are claiming the same victims, suggesting collaboration between ransomware gangs
What This Means for Your Organization:
The traditional "patch and pray" approach is dead. When ransomware groups are sharing victims to amplify pressure, and when they're offering automated negotiation tools, you're not dealing with opportunistic criminals anymore—you're facing sophisticated business operations.
What I'm Seeing in the Field: Three Critical Vulnerabilities
Based on what we learned from the September 29-30 attacks and recent Qilin patterns:
1. The MSP Backdoor Problem
An April 2025 phishing incident analyzed by Sophos involved attackers phishing administrative credentials for the ScreenConnect remote monitoring tool to gain access to an MSP environment. The attackers then used that access to launch downstream ransomware attacks on the MSP's customers.
If you're using managed service providers, you need to audit their security posture immediately. Your vendors are your attack surface now.
2. The Public-Facing Application Weakness
According to PRODAFT, on June 5, 2025, threat actors were actively exploiting FortiGate vulnerabilities to deploy Qilin ransomware. OP Innovate also reports that Qilin-tied infrastructure exploited a SAP NetWeaver vulnerability with a CVSS score of 10 before it was publicly disclosed.
Zero-day exploitation isn't theoretical—it's standard operating procedure for top-tier ransomware groups.
3. The Weak Password Catastrophe
One U.S. state/local/tribal/territorial (SLTT) incident reported to MS-ISAC started with a phishing email. The adversary then targeted a user account with a weak password and unnecessary admin access, creating new admin accounts used to encrypt data network-wide.
Basic security hygiene failures are still creating enterprise-wide disasters.
The Bottom Line: We're in a New Era
The September 29-October 1 period represents an inflection point in ransomware evolution. Qilin topped the charts as the most active ransomware group across all global regions, highlighting the group's significant reach.
What makes this weekend different isn't just the number of attacks—it's the sophistication of the business model behind them. Qilin has built an enterprise that offers:
- Automated attack tools
- Professional negotiation assistance
- Data storage infrastructure
- Marketing support for affiliates
- DDoS capabilities for additional pressure
We're facing adversaries with capabilities that rival legitimate security companies.
The Strategic Question:
The real question isn't whether your organization will be targeted—it's whether you'll be ready when it happens. The organizations that survived this weekend's attacks are the ones that had:
- Isolated backups
- Tested incident response plans
- Rapid decision-making processes
- Vendor security oversight
The ones that didn't? They're negotiating with "in-house journalists" right now.
References
- BreachSense. "Latest Data Breaches and Most Recent Data Breach Incidents." September 30, 2025. https://www.breachsense.com/breaches/
- Cyble. "Qilin Ransomware Group Leads Surge, Sinobi's Rapid Rise." September 2025. https://cyble.com/blog/qilin-ransomware-group-leads-surge/
- Qualys. "Qilin Ransomware Explained | Understanding Cyber Attacks & Defense." June 18, 2025. https://blog.qualys.com/vulnerabilities-threat-research/2025/06/18/qilin-ransomware-explained-threats-risks-defenses
- Barracuda Networks. "Qilin ransomware is growing, but how long will it last?" July 18, 2025. https://blog.barracuda.com/2025/07/18/qilin-ransomware-growing
- The Hacker News. "Qilin Ransomware Ranked Highest in April 2025 with 72 Data Leak Disclosures." May 9, 2025. https://thehackernews.com/2025/05/qilin-leads-april-2025-ransomware-spike.html
- CIS. "Qilin: Top Ransomware Threat to SLTTs in Q2 2025." https://www.cisecurity.org/insights/blog/qilin-top-ransomware-threat-to-sltts-in-q2-2025
- ZTE Corporation. "ZTE and China Mobile Henan Branch jointly showcased AI + 5G New Calling Service and won the ICT award at PT Expo China." September 30, 2025. https://www.zte.com.cn/global/about/news/



