Ransomware Without Encryption: Why Pure Exfiltration Attacks Are Surging in 2026
Your endpoint detection didn't fire a bunch of alerts. Your backup strategy is intact. Your systems are running normally.
And yet, your most sensitive data is already being auctioned on the dark web.
Welcome to ransomware's quiet evolution: pure exfiltration attacks—campaigns that skip encryption entirely and extort victims based solely on stolen data. Recognizing this shift helps security professionals feel responsible for adapting defenses as we enter February 2026, when this strategy has become dominant, leaving organizations unprepared.
The Silent Shift in Ransomware Tactics
Traditional ransomware followed a predictable playbook: infiltrate, encrypt, demand payment for decryption keys. Security teams built entire defense strategies around this model—robust backups, endpoint detection and response (EDR), and network segmentation to limit blast radius.
Attackers noticed. And they adapted.
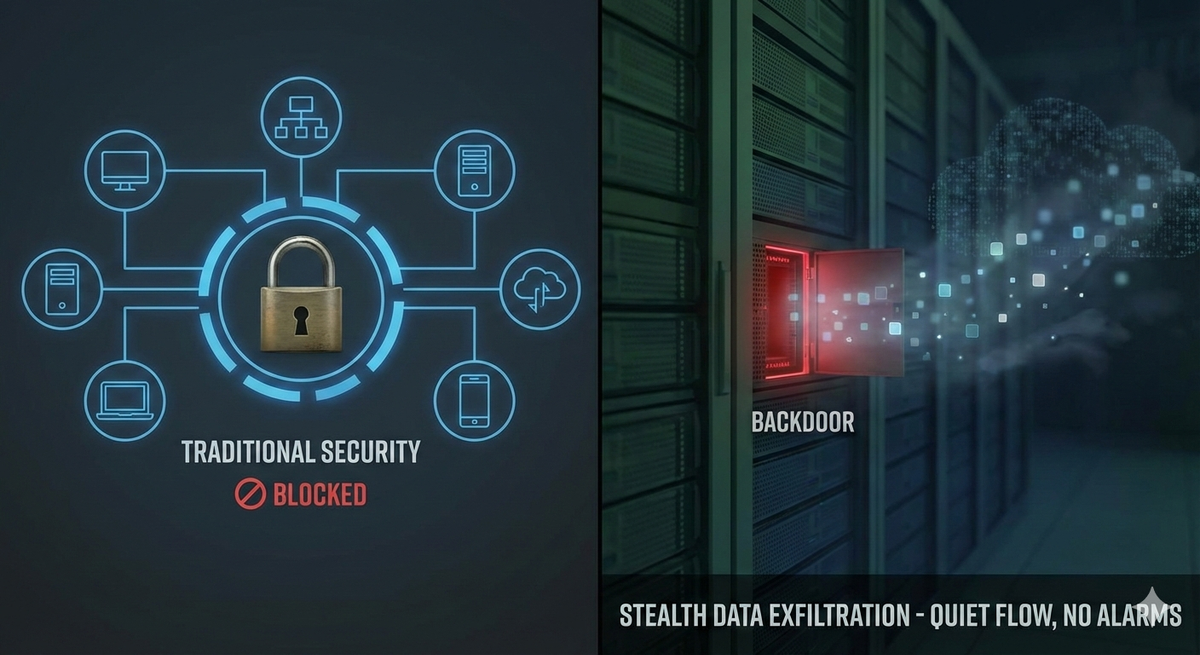
According to recent industry analysis, many ransomware attacks no longer involve encryption. Instead, threat actors quietly exfiltrate sensitive data—sometimes over weeks or months—and then extort victims long after the initial breach. The rationale is devastatingly simple: why trigger every alarm in the building when you can walk out the front door with the valuables?
This shift explains why the number of active ransomware groups increased by approximately 30% compared to 2024, even as law enforcement disrupted major syndicates. The barrier to entry dropped dramatically when attackers realized they didn't need sophisticated encryption capabilities—just patience and data movement tools.
Why Exfiltration-Only Attacks Are Harder to Detect
The challenge for defenders is fundamental: your security stack is optimized for the wrong threat model.
Most EDR solutions prioritize detecting encryption behaviors—mass file modifications, suspicious process execution, and known ransomware signatures. Pure exfiltration attacks trigger none of these indicators. Instead, they leverage:
- Living off the land techniques using legitimate tools like PowerShell, WinSCP, and cloud sync utilities
- Low-and-slow data transfer that stays below bandwidth anomaly thresholds
- Compromised credentials that make malicious access appear legitimate
- Cloud storage abuse where data flows to attacker-controlled accounts via sanctioned platforms
The Sedgwick Government Solutions breach, disclosed in early 2026, exemplifies this pattern. The TridentLocker ransomware gang reportedly extracted 3.4 gigabytes of data from a subsidiary serving federal agencies, including DHS, ICE, and CBP—without triggering the kind of operational disruption that typically alerts security teams.
The Business Case Attackers Are Making
From the attacker's perspective, exfiltration-only campaigns offer superior economics:
- Lower operational risk: No encryption means no immediate incident response activation
- Extended dwell time: Attackers can return repeatedly to extract additional data
- Regulatory leverage: HIPAA, GDPR, and state privacy laws create compliance pressure independent of operational impact
- Reputational ammunition: The threat of public disclosure often exceeds the effects of temporary system outages
The recent MACT Health Board breach in California's Sierra Foothills demonstrates this leverage in healthcare settings. When the Rhysida ransomware group compromised patient medical records, the extortion pressure wasn't about restoring operations—it was about preventing disclosure of sensitive health information that could trigger regulatory investigation and patient lawsuits.
Five Critical Gaps in Your Current Defense Posture
Based on incident response patterns across multiple sectors, these are the most common defensive gaps enabling exfiltration success:
1. Inadequate Data Loss Prevention (DLP) Coverage
Most organizations deploy DLP at email gateways while ignoring cloud storage, USB devices, and web uploads. Attackers route exfiltration through unmonitored channels.
2. Missing Behavioral Analytics on Legitimate Tools
When rclone.exe or cloud sync utilities transfer gigabytes of data, does your SIEM correlate that with the user's normal behavior? For most organizations, the answer is no.
3. Over-Reliance on Perimeter Defenses
Zero Trust architectures remain aspirational for many enterprises. Without internal traffic inspection and microsegmentation, lateral movement and data staging go undetected.
4. Insufficient Logging Retention
Exfiltration attacks with extended dwell times require months of log data for forensic reconstruction. Many organizations retain logs for 30-90 days—far short of what's needed.
5. Credential Hygiene Failures
Compromised credentials remain the primary initial access vector. Weak password policies, lack of MFA on internal systems, and excessive standing privileges create persistent exposure.
Building an Exfiltration-Resistant Security Posture
Defending against data theft extortion requires shifting from "prevent encryption" to "protect data movement." Here's a practical framework:
Implement Data-Centric Security Controls
- Deploy DLP across all egress points: email, web, cloud, and endpoints
- Classify sensitive data and apply controls based on content, not just location
- Monitor for bulk data access patterns that deviate from baseline behavior
Enhance Network Visibility
- Implement network detection and response (NDR) with full packet capture capabilities
- Deploy SSL/TLS inspection at network boundaries (with appropriate privacy controls)
- Establish baseline traffic patterns and alert on anomalous data flows
Harden Identity and Access
- Enforce MFA universally—including for internal applications and privileged access
- Implement just-in-time access provisioning to eliminate standing privileges
- Deploy user and entity behavior analytics (UEBA) to detect credential abuse
Extend Detection Capabilities
- Configure EDR to alert on legitimate tool abuse (PowerShell, archiving utilities, sync tools)
- Integrate threat intelligence focused on exfiltration infrastructure
- Extend log retention to a minimum of 12 months for critical systems
Prepare for Extortion Scenarios
- Develop incident response playbooks specifically for data theft without encryption
- Establish legal and communications protocols for extortion demands
- Consider cyber insurance policies that cover pure exfiltration events
Common Mistakes to Avoid
Assuming backups solve the problem. Robust backup strategies address encryption-based attacks. They do nothing to address data theft or extortion.
Treating DLP as a compliance checkbox. DLP implementations focused solely on regulatory keywords miss the bulk data transfers that characterize exfiltration attacks.
Ignoring insider threat indicators. The behavioral patterns of malicious insiders and external attackers using compromised credentials are nearly identical. Your detection capabilities should address both.
Underestimating dwell time. Industry data suggests average attacker dwell time continues to extend as exfiltration-focused campaigns prioritize stealth over speed.
The Path Forward
The evolution toward exfiltration-only ransomware represents a fundamental shift in adversary tradecraft—one that exposes the limitations of security strategies built for a different threat model.
Organizations that recognize this shift and adapt their defensive posture accordingly will be positioned to detect and disrupt these campaigns before significant data loss occurs. Those who don't will find themselves facing extortion demands for breaches they never knew happened.
The 2026 threat landscape demands that security leaders move beyond endpoint-centric thinking toward comprehensive data protection. The attackers have already made this transition. It's time defenders caught up.
Sources
- Morphisec: Ransomware Without Encryption: Why Pure Exfiltration Attacks Are Surging
- SecurityWeek: Sedgwick Confirms Cyberattack on Government Subsidiary
- The Record: Sedgwick Cyber Incident Affecting Federal Contractor
- Cyble: 10 New Ransomware Groups of 2025 & Threat Trends for 2026
- SecurityWeek: 8,000 Ransomware Attacks Statistics
- Malwarebytes: Under Armour Ransomware Breach